How oauth works diagram
Home » Background » How oauth works diagramYour How oauth works diagram images are available in this site. How oauth works diagram are a topic that is being searched for and liked by netizens now. You can Get the How oauth works diagram files here. Get all royalty-free vectors.
If you’re searching for how oauth works diagram images information connected with to the how oauth works diagram interest, you have pay a visit to the right blog. Our website frequently gives you suggestions for seeing the maximum quality video and image content, please kindly surf and find more enlightening video articles and images that fit your interests.
How Oauth Works Diagram. In this section I will explain you in a technical way. The OAuth 20 authorization code flow is described in section 41 of the OAuth 20 specification. These specifications are completely different from one another and cannot be used together. This diagram is from httpsblogoauthiointroduction-oauth2-flow-diagrams.
 Diagrams And Movies Of All The Oauth 2 0 Flows By Takahiko Kawasaki Medium From darutk.medium.com
Diagrams And Movies Of All The Oauth 2 0 Flows By Takahiko Kawasaki Medium From darutk.medium.com
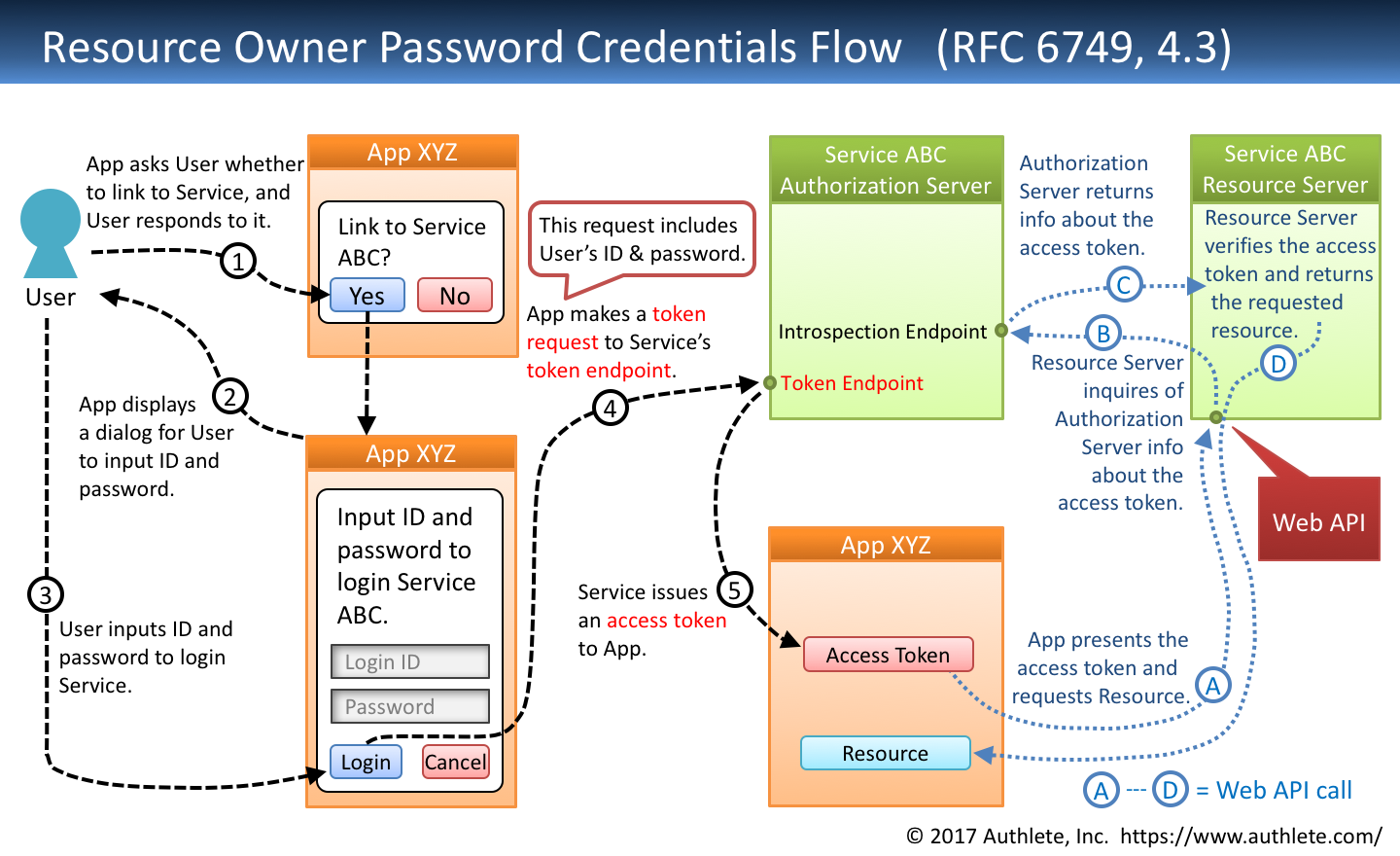
The steps to grant permission or consent are often referred to as authorization or even delegated authorization. In this step when the Resource owner clicks on Connect with Google button then request will go to the Authorization Server along with Redirect URL and Response Type. In principle the Get Access Token flow has 5 steps as shown in the diagram below. OAuth Server authenticates user when she clicks on the Apps social login button which is tagged with Client ID. There are two versions of OAuth. App client acquires access token.
The OAuth client initiates the flow when it directs the user agent of the resource owner to the authorization endpoint.
OAuth 20 Flow Diagram Explanation of OAuth 20 Diagram. This diagram is from httpsblogoauthiointroduction-oauth2-flow-diagrams. The steps to grant permission or consent are often referred to as authorization or even delegated authorization. Configuration enableauthorizationserver public class oauth2authorizationserver extends as shown in the above sequence diagram the first step is to get authorization grant from. In this section I will explain you in a technical way. The sequence diagram below demonstrates the oauth 20 device flow the following sequence diagram shows how the client gains access to protected resources in the scenario where am functions as both authorization server and client for example.
 Source: pinterest.com
Source: pinterest.com
OAuth is an authorization protocol rather than an authentication protocol. Implement OAuth 20 with Azure AD. OAuth 20 is a security standard where you give one application permission to access your data in another application. OAuth Server authenticates user when she clicks on the Apps social login button which is tagged with Client ID. OAuth works over HTTPS and authorizes devices APIs servers and applications with access tokens rather than credentials.
 Source: researchgate.net
Source: researchgate.net
The sequence diagram below demonstrates the oauth 20 device flow the following sequence diagram shows how the client gains access to protected resources in the scenario where am functions as both authorization server and client for example. In this step when the Resource owner clicks on Connect with Google button then request will go to the Authorization Server along with Redirect URL and Response Type. The OAuth 20 authorization code flow is described in section 41 of the OAuth 20 specification. Your app must be server-side because during this exchange you must also pass along your. How OAuth works.
 Source: pinterest.com
Source: pinterest.com
OAuth is a specification as to how to issue access tokens. In this step when the Resource owner clicks on Connect with Google button then request will go to the Authorization Server along with Redirect URL and Response Type. In principle the Get Access Token flow has 5 steps as shown in the diagram below. OAuth provider request user to grant permission to your app client OAuth provider issues code. There are two versions of OAuth.
 Source: spanning.com
Source: spanning.com
Designed to work specifically with Hypertext Transfer Protocol HTTP OAuth separates the role of the client from the resource owner. The steps to grant permission or consent are often referred to as authorization or even delegated authorization. The flow enables apps to securely acquire access_tokens that can be used to access resources secured by the Microsoft identity platform as well as refresh tokens to get additional access_tokens and ID tokens for the signed in user. Implement OAuth 20 with Azure AD. Step 2 Next the client application will be provided with the client id and client password during registering the redirect URI.
 Source: in.pinterest.com
Source: in.pinterest.com
In this section I will explain you in a technical way. OAuth is an authorization protocol rather than an authentication protocol. Understand in very simple words. Application for using OAuth in ownCloud. These specifications are completely different from one another and cannot be used together.
 Source: youtube.com
Source: youtube.com
Because regular web apps are server-side apps where the source code is not publicly exposed they can use the Authorization Code Flow defined in OAuth 20 RFC 6749 section 41 which exchanges an Authorization Code for a token. Implement OAuth 20 with Azure AD. The OAuth client includes its client identifier requested scope local state and a redirection URI. Using OAuth on its own as an authentication method may be referred to as pseudo-authentication. Its used to perform authentication and authorization in the majority of app types including single page apps web apps and natively installed apps.
 Source: pinterest.com
Source: pinterest.com
OAuth 20 - Architecture. The authorization code workflow diagram involves the following steps. The application requests authorization to access service resources from the user. Citation needed The following diagrams highlight the differences between using OpenID specifically designed as an authentication protocol and OAuth for authorization. This diagram is from httpsblogoauthiointroduction-oauth2-flow-diagrams.
 Source: in.pinterest.com
Source: in.pinterest.com
Resource Owner choose to Sign up with Google. In this section I will explain you in a technical way. The steps to grant permission or consent are often referred to as authorization or even delegated authorization. This diagram is from httpsblogoauthiointroduction-oauth2-flow-diagrams. In this section I will explain you in a technical way.
 Source: pinterest.com
Source: pinterest.com
Because regular web apps are server-side apps where the source code is not publicly exposed they can use the Authorization Code Flow defined in OAuth 20 RFC 6749 section 41 which exchanges an Authorization Code for a token. OAuth is often used by tech giants to authorize third-party apps to provide access over restricted resources that resides in a. Application for using OAuth in ownCloud. It allows a user to grant limited access to its protected resources. It is defined in RFC The OAuth Authorization Framework.
 Source: pinterest.com
Source: pinterest.com
OAuth Open Authentication is a unique access token based authentication over the internet. OAuth is often used by tech giants to authorize third-party apps to provide access over restricted resources that resides in a. OAuth 20 is a security standard where you give one application permission to access your data in another application. Pre-register Client App with OAuth Server to get Client IDClient Secret. OAuth is a specification as to how to issue access tokens.
 Source: darutk.medium.com
Source: darutk.medium.com
The OAuth 20 is the industry protocol for authorization. There are 3 main players in an OAuth transaction. It is defined in RFC The OAuth Authorization Framework. Step 2 Next the client application will be provided with the client id and client password during registering the redirect URI. This triumvirate has been affectionately deemed the OAuth Love Triangle.
 Source: pinterest.com
Source: pinterest.com
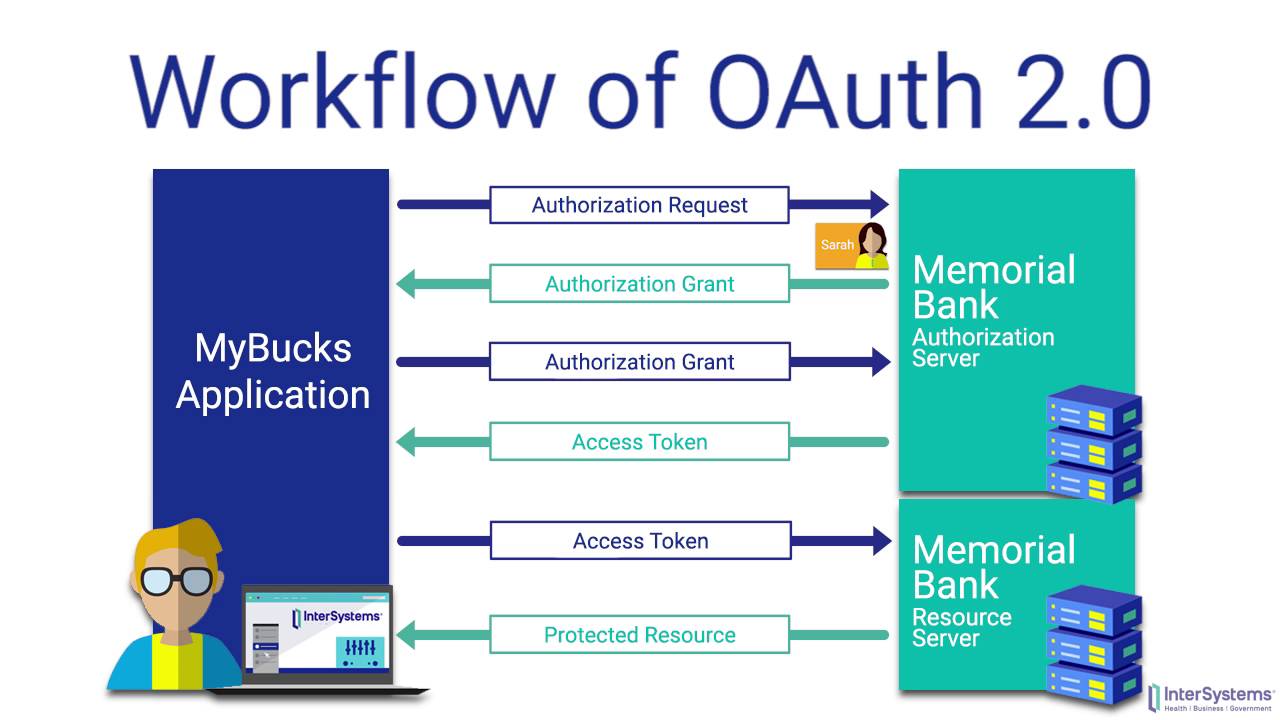
The application requests authorization to access service resources from the user. In our example Joe is the user Bitly is the consumer and Twitter is the service provided who controls Joes secure resource his Twitter stream. In this step when the Resource owner clicks on Connect with Google button then request will go to the Authorization Server along with Redirect URL and Response Type. There is no backwards compatibility between them. It lets users authorize third-party access to their servers without handing out their username and password.
 Source: pinterest.com
Source: pinterest.com
In our example Joe is the user Bitly is the consumer and Twitter is the service provided who controls Joes secure resource his Twitter stream. How OAuth works. It lets users authorize third-party access to their servers without handing out their username and password. In this chapter we will discuss the architectural style of OAuth 20. OAuth is an open standard for authorization.
 Source: pinterest.com
Source: pinterest.com
OAuth Server authenticates user when she clicks on the Apps social login button which is tagged with Client ID. In this step when the Resource owner clicks on Connect with Google button then request will go to the Authorization Server along with Redirect URL and Response Type. There is no backwards compatibility between them. The client requests access to the resources. In our example Joe is the user Bitly is the consumer and Twitter is the service provided who controls Joes secure resource his Twitter stream.
 Source: pinterest.com
Source: pinterest.com
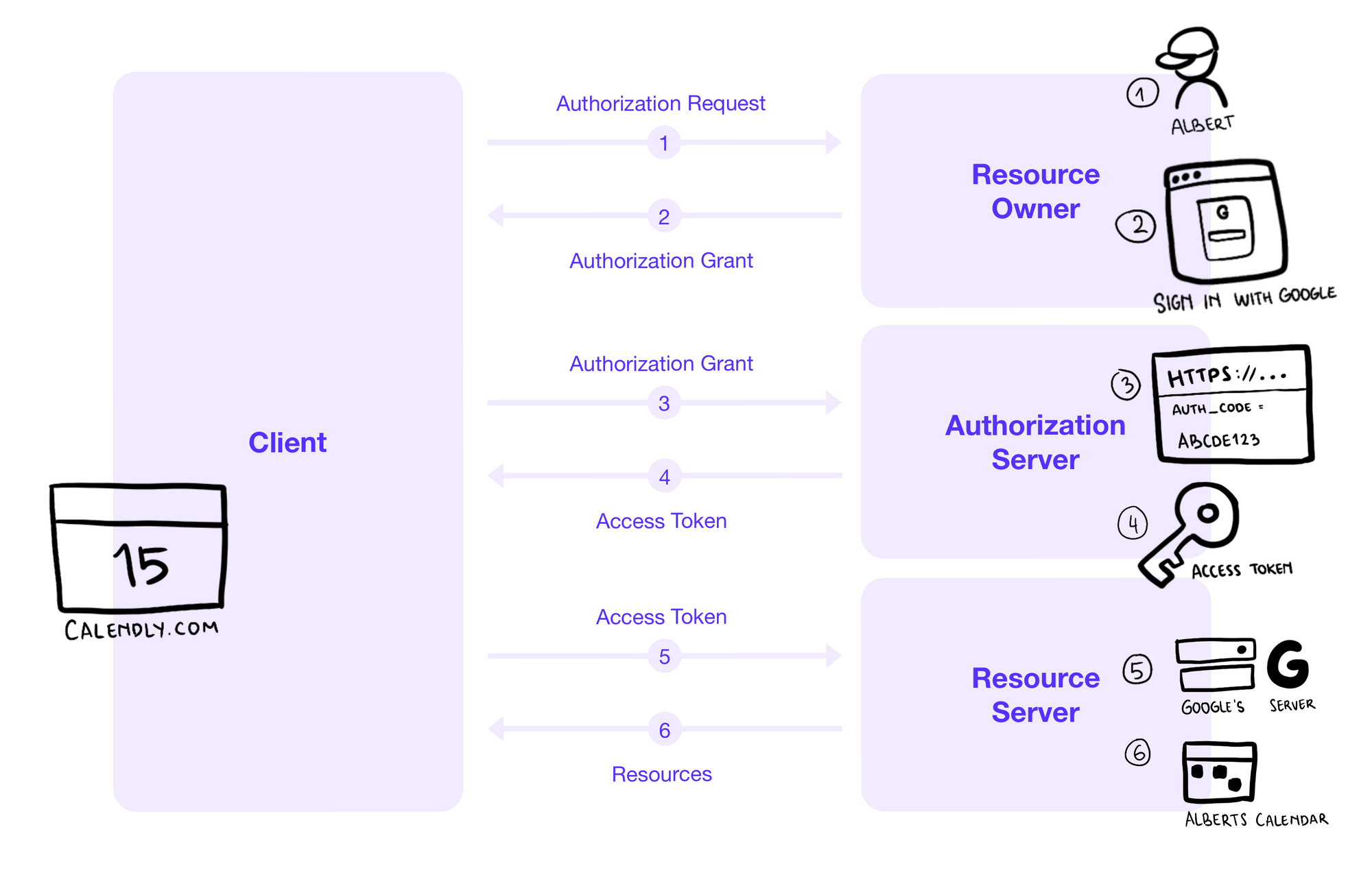
There are 3 main players in an OAuth transaction. In this section I will explain you in a technical way. Here is a more detailed explanation of the steps in the diagram. Pre-register Client App with OAuth Server to get Client IDClient Secret. OAuth 10a and OAuth 20.
 Source: freesin.trasportopiu.it
Source: freesin.trasportopiu.it
The flow enables apps to securely acquire access_tokens that can be used to access resources secured by the Microsoft identity platform as well as refresh tokens to get additional access_tokens and ID tokens for the signed in user. OAuth 2 is an authorization framework that enables applications to obtain Here is a more detailed explanation of the steps in the diagram. The OAuth 20 is the industry protocol for authorization. Pre-register Client App with OAuth Server to get Client IDClient Secret. Step 2 Next the client application will be provided with the client id and client password during registering the redirect URI.
 Source: pinterest.com
Source: pinterest.com
OAuth 10a and OAuth 20. The flow enables apps to securely acquire access_tokens that can be used to access resources secured by the Microsoft identity platform as well as refresh tokens to get additional access_tokens and ID tokens for the signed in user. Citation needed The following diagrams highlight the differences between using OpenID specifically designed as an authentication protocol and OAuth for authorization. Step 1 First the user accesses resources using the client application such as Google Facebook Twitter etc. There are two versions of OAuth.
 Source: pinterest.com
Source: pinterest.com
OAuth framework enables client applications by using delegation pattern in which certain functionalities can be delegated to an existing resource server without replicating the same feature Eg. OAuth Open Authentication is a unique access token based authentication over the internet. There are 3 main players in an OAuth transaction. OAuth framework enables client applications by using delegation pattern in which certain functionalities can be delegated to an existing resource server without replicating the same feature Eg. OAuth 20 - Architecture.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how oauth works diagram by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.